I wrote this guide to take you from zero to a working understanding of the security platform and what it does. I explain how the solution unifies XDR and SIEM to protect on‑premises, virtualised, containerised and cloud workloads. The aim is practical clarity so you can plan deployment and operation.
I will set expectations about suitability and scope. The platform is free and open source, making it suitable for individuals, small teams and enterprises that value transparency and customisation. You will learn which environments are in scope from day one.
I outline the platform structure: three central components and a universal agent, plus a web interface for analysis and access. I also signpost two paths to start — an automated Quickstart that installs in minutes, and a full installation guide if you prefer control.
Get your copy now. PowerShell Essentials for Beginners – With Script Samples

Get your copy now. PowerShell Essentials for Beginners – With Script Samples
In short
- You will grasp what the platform protects and where it fits in defence‑in‑depth.
- The solution is open source and practical for varied team sizes.
- Coverage includes on‑premises, virtual, container and cloud workloads.
- There are three core components, a universal agent, and a web interface for management.
- You can try the SaaS option with a 14‑day trial to evaluate without provisioning.
What is Wazuh and why beginners choose this open source security platform

I will clarify what the platform actually protects and why it appeals to those just starting with monitoring. My aim is clear: give practical meaning without jargon.
Understanding SIEM and XDR in plain terms
SIEM can be summarised as SEM + SIM = SIEM. That means real‑time event handling and correlation paired with historical log retention and analysis.
Core features you should see on day one:
- Log collection and retention that preserves important data.
- Real‑time event correlation and user activity monitoring.
- Rules, CTI integration, reporting and visual dashboards to act on alerts.
Why open source matters
I recommend open source because it offers cost control, freedom to customise, and fewer licence limits as you scale. Community contributions speed fixes and feature parity with commercial solutions.
Common use cases and deployments
The solution protects on‑premises racks, virtual clusters, container orchestrations such as Kubernetes, and major public cloud services.
- Uniform monitoring across varied systems and network layouts.
- Start small with a pilot subnet to reduce risk and learn fast.
This guide will walk you from concept to hands‑on steps while keeping those expectations in view.
Inside the Wazuh platform: components, architecture, and data flow
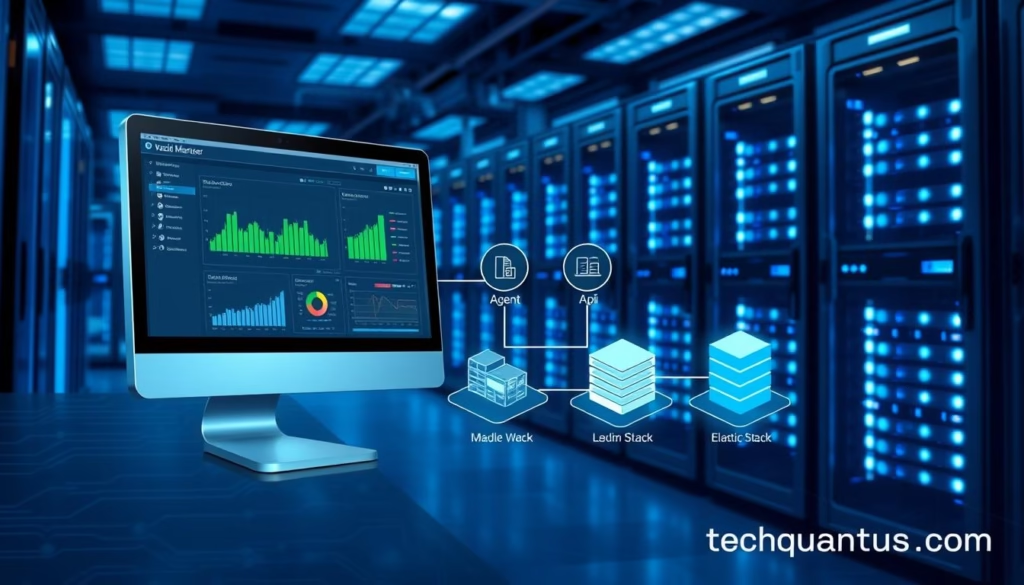
I map how each core component connects so you can see where telemetry is created, processed and analysed. This section shows the actors involved and the path an event takes from endpoint to dashboard.
Agent coverage across common operating systems
The universal wazuh agent runs on Windows, Linux and macOS as well as several enterprise UNIX variants. Agents collect logs, monitor files, detect hidden processes and flag anomalies at source.
Server processing and threat enrichment
The wazuh server ingests that telemetry, applies decoders and rules, and uses threat intelligence to mark IOC hits. The server scales via clustering so it can handle thousands of endpoints.
Indexing, dashboards and agentless sources
Elastic indexes alerts and stores searchable information. The Kibana-based web interface provides dashboards, saved searches and pivoting across timelines.
- I explain when to use agents versus agentless Syslog for network appliances.
- I trace the flow: collection, normalisation, rule matching, enrichment and persistence.
- These choices improve mean time to detect by ensuring the right data reaches the right place.
Wazuh for Beginners: A Comprehensive Guide to installation options

Choose a fast automated path, a hands‑on manual installation, or a hosted service; each suits different goals and teams.
Quickstart deployment to get running in minutes
Quickstart uses automation to install core pieces rapidly. It lowers friction and gets telemetry flowing in minutes.
That path remains production‑relevant while you learn. Use it to validate use cases quickly and verify your web access to the dashboard.
Full installation guide: configuring each central component
The full guide walks through each central component so you can tune resources, harden security and scale intentionally.
Follow the documentation to deploy the manager, indexer, dashboard and beats and to record decisions for later audits.
Wazuh Cloud: SaaS service, 14‑day trial, and when to choose it
If you want to avoid infrastructure overhead, the managed cloud option gives a 14‑day trial to validate features before committing to self‑hosted deployment.
| Option | Includes | Best for |
|---|---|---|
| Quickstart | Automated install, basic tuning | Fast proof of value |
| OVA import | Manager, Indexer, Dashboard, Filebeat | Lab or virtualised server setup |
| Full install | Fine‑tuned components and hardening | Production with custom scaling |
| Cloud service | Managed hosting, trial available | Teams avoiding infra ops |
After install, set admin credentials, confirm agent endpoints and check index health. Start small: one server, a few test nodes and a focused use case such as FIM. Good notes and the official documentation make later scale‑out or a move to a managed cloud straightforward.
Step‑by‑step: deploying Wazuh agents on your endpoints
I explain the sequence I use to install agents on diverse systems and confirm they report data to the server. Start by preparing a test host, then expand the rollout once registration and monitoring look healthy.
Linux endpoints: add the official repository, install the wazuh agent package, edit the agent configuration to point to the Manager IP or hostname, then start and enable the systemd service so the agent survives reboots.
Windows endpoints: download the agent installer and run it via the GUI or CLI. Enter the manager connectivity details during setup, start the service, and confirm the host can reach the Manager IP over the required ports.
I verify registration from both sides. On the endpoint I check the agent status and logs. On the server I watch the dashboard for heartbeats and incoming events. This proves that monitoring and data flow are working.
Common mistakes include typos in the Manager address, DNS issues and blocked ports. Troubleshoot using the agent logs: /var/ossec/logs/ossec.log on Linux and C:\Program Files (x86)\ossec-agent\ossec.log on Windows.
| Step | Linux | Windows |
|---|---|---|
| Prepare host | Enable 64‑bit virtualization on host; add repository | Confirm networking; download installer |
| Install agent | apt/yum install wazuh-agent package | Run MSI via GUI or msiexec CLI |
| Configure | Edit /var/ossec/etc/ossec.conf to set manager IP | Enter manager IP during install; verify service config |
| Start & enable | systemctl enable –now wazuh-agent | Start service and set to Automatic |
| Verify | Check /var/ossec/logs/ossec.log and agent status | Check C:\Program Files (x86)\ossec-agent\ossec.log and service |
For an OVA‑based server, ensure the host supports 64‑bit guests and has VirtualBox or VMware ready. I recommend a small, mixed rollout of workstations and servers to confirm coverage and to watch event volume rise as endpoints come online.
Core security capabilities you can enable from day one
You can enable several high‑value security controls right away; I explain which ones and why they matter.
Intrusion detection and real‑time event correlation
Agents capture events on hosts and stream them to the server. The server uses decoders, rules and threat feeds to correlate events across systems and surface high‑confidence alerts quickly.
File integrity monitoring and configuration assessment
I enable FIM on critical paths to detect unexpected changes. Combining those change events with configuration assessment helps flag insecure settings early and reduce drift.
Vulnerability detection and incident response
Scheduled scans produce vulnerability data that I map to tickets and playbooks. This moves issues from detection to closure and supports efficient incident response workflows.
Regulatory compliance, reports, and visualisation dashboards
The Elastic/Kibana interface organises alerts and compliance information into dashboards. I use these to prioritise findings and to gather evidence auditors recognise.
Cloud and container security monitoring across services and networks
I bring telemetry from cloud services and orchestration layers into the same monitoring view. This unifies container and host events so analysis happens in one place.
| Capability | Components | Quick win |
|---|---|---|
| Intrusion detection | Agents, server rules, threat feeds | Enable core ruleset and heartbeat checks |
| FIM & config | Agents, file watches, config policies | Watch /etc and critical binaries |
| Vuln & IR | Scanner, tickets, playbooks | Schedule weekly scans and map to tickets |
Tip: start small with high‑value checks and test changes safely. The transparent, open source rules and decoders let you tune sensitivity without surprises.
Operations, configuration, and troubleshooting at the present time
My aim here is to make routine checks and common fixes quick and repeatable.
Connectivity checks between server and agents
I start by verifying the Manager IP is correct on each agent and that name resolution works. Test the network path with ping, traceroute or your preferred tool to isolate link issues quickly.
I then confirm the server shows active registrations and recent heartbeats via the web interface. That tells me the host is sending data and the server is accepting connections.
Reading logs and resolving common issues
When problems arise, I read the logs in the right place: /var/ossec/logs/ossec.log on Linux and C:\Program Files (x86)\ossec-agent\ossec.log on Windows. I scan for time‑correlated errors to pinpoint the root cause.
Common fixes include correcting the Manager address, unblocking network ports, and ensuring credentials match. After importing the OVA I confirm web access to the dashboard and verify my account has the needed access to view agent status.
“Verify connectivity, credentials, configuration, logs and platform health in that order to close the loop fast.”
- I validate system prerequisites: a 64‑bit host, virtualisation enabled and a working hypervisor.
- I document recurring issues and link fixes to official documentation so resolution time drops on repeat incidents.
- I record the exact time and parameters when changing configuration so I can correlate effects across logs and the interface.
- I run periodic drills to reduce time from alert to resolution in real conditions.
| Check | Action | Why it matters |
|---|---|---|
| Network | Ping/traceroute, confirm DNS | Isolates link and name resolution issues |
| Logs | Inspect agent and server logs | Find time‑correlated errors that reveal configuration gaps |
| Dashboard | Confirm heartbeats, registrations, and access | Shows agents are sending data and you can view it |
Conclusion
To finish, I set out a short action plan that moves you from install to effective detection. This guide summarises the path from learning SIEM and XDR basics to standing up a wazuh server and rolling out the wazuh agent across endpoints. Start with one use case and validate alert quality before you expand.
Agents and agentless inputs combine to gather the data you need from endpoints and network devices. The server scales via clustering and integrates with Elastic so dashboards stay useful as your system grows.
Choose self-managed builds or the managed service that suits your team. Verify connectivity, read the right logs and keep a repeatable troubleshooting routine. Pick a small deployment, document changes, then iterate—security improves over time.
FAQ
What is this security platform and who should consider it?
I explain that this open source security platform combines SIEM and extended detection and response capabilities to protect endpoints, servers and cloud workloads. I recommend it to small teams that need cost-effective monitoring, to administrators seeking customisation, and to operations teams managing hybrid environments.
How does the agent work across different operating systems?
I describe that the agent runs on Windows, Linux and macOS to collect logs, file integrity events and system metrics. It sends data securely to the central server, supports policy-driven configuration, and can be managed at scale through the platform’s management layer.
What are the main components I must install?
I outline the essentials: the central server that processes rules and decoders, the data store and search layer (Elastic Stack), and the web interface for dashboards. Agents or agentless collectors provide the telemetry from hosts and network devices.
Can I start with a quick deployment and upgrade later?
I confirm you can use a quickstart to get running in minutes for testing and proof of concept. Later, you can perform a full installation with hardened configuration, high availability and scalability for production use.
When should I choose the managed cloud service instead of self‑hosting?
I advise choosing the managed cloud service if you want faster onboarding, reduced operational overhead and a trial to evaluate features. Self‑hosting suits teams that require full control over data, bespoke integrations or on‑premises compliance.
How do I deploy agents on Linux and Windows?
I summarise that Linux deployment uses distribution repositories or packages and standard service management. Windows supports MSI installers and CLI options; both require registration with the manager and verification through the web interface.
How can I verify agents are connected and sending data?
I recommend checking the manager’s agent list in the web UI, reviewing agent logs locally, and confirming incoming events in the index. Simple connectivity tests and authentication checks help isolate network or certificate issues.
What core security features are available out of the box?
I list key features such as intrusion detection, real‑time event correlation, file integrity monitoring, vulnerability detection and compliance reporting. Dashboards and alerts let you monitor incidents and respond quickly.
Does the platform support container and cloud service monitoring?
I explain that it supports monitoring containerised workloads and cloud services via native integrations, log collectors and API connectors, enabling visibility across Kubernetes, public cloud instances and networked services.
How do I troubleshoot common connectivity and configuration issues?
I suggest starting with connectivity checks between agents and server, validating certificates, and inspecting logs on both ends. Known issues often relate to firewall rules, time skew or misconfigured decoders, and addressing those resolves most problems.
Related posts:
 CISSP Domain 2: Guide to Asset Security Fundamentals
CISSP Domain 2: Guide to Asset Security Fundamentals
 CISSP Domain 3: Security Architecture and Engineering
CISSP Domain 3: Security Architecture and Engineering
 Explore CISSP Domain 5: Identity & Access Management
Explore CISSP Domain 5: Identity & Access Management
 How to Implement Cybersecurity Measures for Your Business
How to Implement Cybersecurity Measures for Your Business
 How I Use Wazuh + AI to Turn SIEM Alerts into Actionable Playbooks with LLMs
How I Use Wazuh + AI to Turn SIEM Alerts into Actionable Playbooks with LLMs
 Quantum Computers Decrypting Blockchain: The Risks and Implications
Quantum Computers Decrypting Blockchain: The Risks and Implications









