
The Revolution of Modern Payment Apps: Security and Ease to Use
Explore how modern payment apps revolutionize transactions with enhanced security features and streamlined ease of use for your monetary exchanges.

Explore how modern payment apps revolutionize transactions with enhanced security features and streamlined ease of use for your monetary exchanges.

Explore how Blockchain technology can revolutionize your transactions, ensuring security and trust in every exchange. Embrace the future of finance.

Learn how to enhance your threat detection capabilities with AI-powered cybersecurity automation for more efficient and effective security operations.

Discover how Extended Reality (XR) can revolutionize your business training programs with immersive, interactive learning experiences.

Discover how to safeguard your digital assets with crucial steps to setup your cloud security. Protect your data effectively with our expert guide.

Unlock the strategies for robust Cloud Security in multi-cloud environments with cutting-edge tools and best practices for 2024.

Explore how IT Firewalls and VPNs collaborate to enhance your network security, safeguarding your online privacy and data integrity.
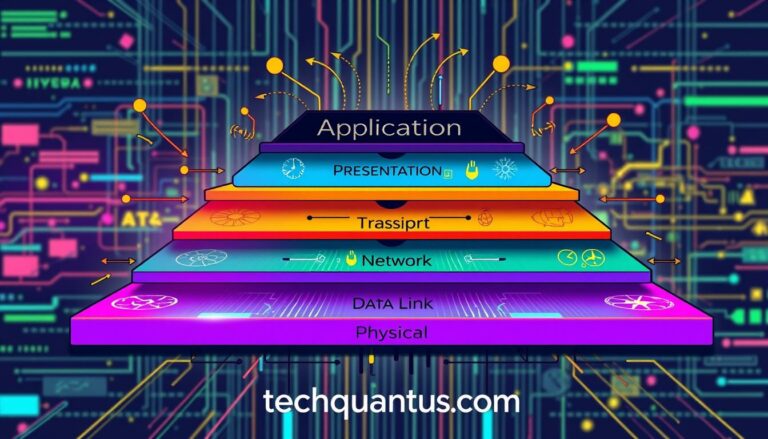
Unveil the OSI Model essentials and explore the seven pivotal layers that form the backbone of modern networking techniques.

Uncover key strategies for Network Security, ensuring your data and infrastructure are shielded against evolving cyber threats.

Explore the fundamentals of Access Control Concepts to protect your systems and ensure data integrity in cybersecurity initiatives.
© 2023 – 2024. All Rights Reserved